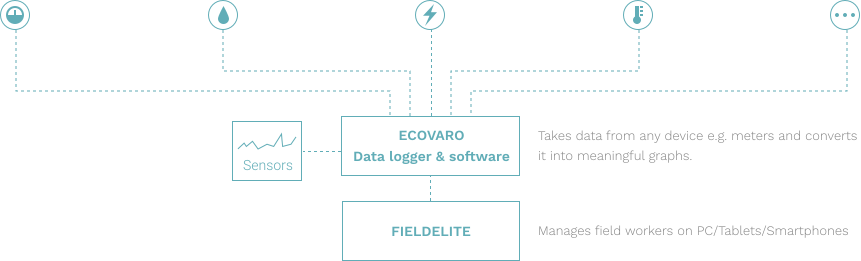
Smart Environmental Dashboards
A solution integrating Meraki Wi-Fi routers, cameras, and environmental sensors to provide people-counting, environmental monitoring, and automated access control, primarily for town councils and public spaces.
- Real-Time Analytics
- Seamless Access Integration
- Built on Cisco Meraki Ecosystem