Building up any business is already hard, more so when it involves providing field services.
A field service business owner has to manage the usual tasks, like scheduling jobs efficiently or inventory checks, and you have to do it while your employees are scattered about on various locations.
It’s the reason FieldElite was created, to provide companies with a much better way to manage and monitor their field workers.
Aside from effective management for your workforce on the move, field service management software can also help your business grow.
5 Ways Using Field Service Management Software Grows Your Business
1. Management Integration
You replace manual field service processes. If your business also uses other management apps, like CRM, payroll, industry-specific software, etc., make sure to integrate them with your chosen field service management software.?
Make those software work side-by-side with your field service management app to achieve streamlined business management.
Integration also removes the possibility of duplicate input on the regular system used and your field service management software, maximising your efficiency and business growth.
2. Improved Tracking
Utilising a field service management software gives you better tracking of every aspect of your field service business.
- Track your inventory numbers in real-time ? know exactly how much stock is on hand for parts, and when it’s time to order more
- Constant updates on Key Performance Indicators ? ensure your business is running smoothly
- First-time fix rates tracking ? avoid wrong rate application
- Monitor your technician?s performance ? ensuring quality work, in turn, profit.
Grow your business by having improved tracking on meaningful data and analytics produced from your field service management software.
3. Cost Cutting
Cutting costs can improve your bottom line and a lot of businesses turn to laying off technicians to cut costs. With a field service management software, there?s no need to go this route.
You cut costs through no manual processes needing to be completed. No need to hire back-office staff to field service calls or produce paperwork orders.
Your field service software should have all your automated needs met for efficient field job management.
An example of cost-cutting using field service app:
Track how much your technicians drive and find alternate routes for them to take.
- Reduce gas expenses
- Reduce repair bills for the truck
- Finding better alternate routes can give more time to get to more jobs
- Increased efficiency for the field technician
4.? Mobile Adaptability
Field service companies are focusing on mobility to grow their business. With a field service management software, technicians have on hand the tools and information needed to complete their job.
Field technicians can utilise the following field service software features:
- Limit how much time they spend completing administrative work with the automated work-order management
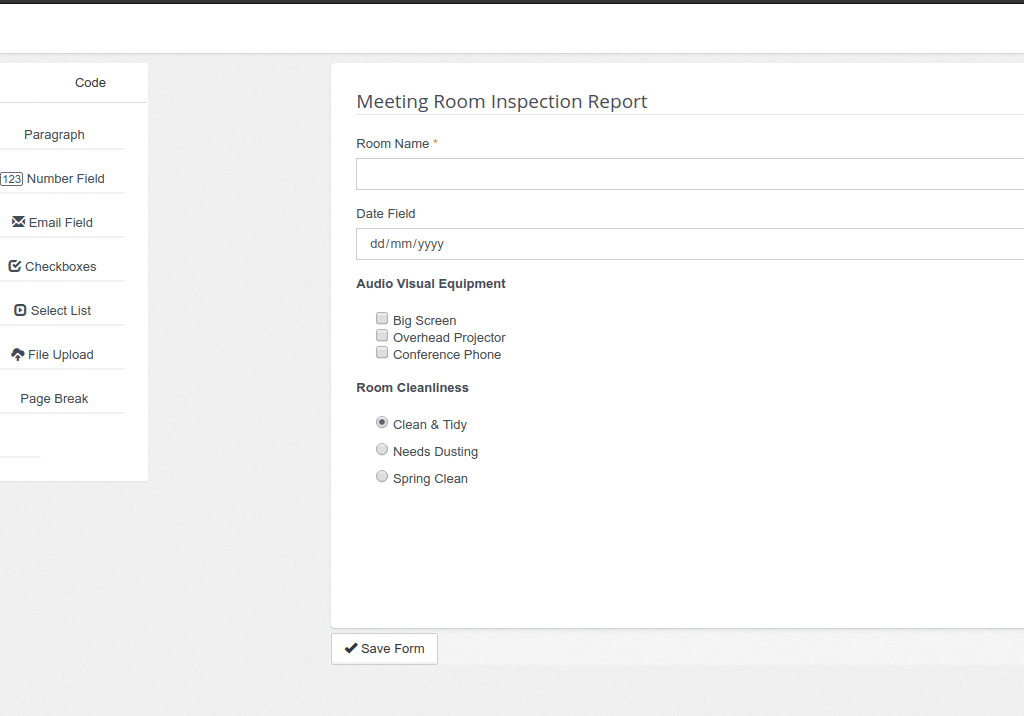
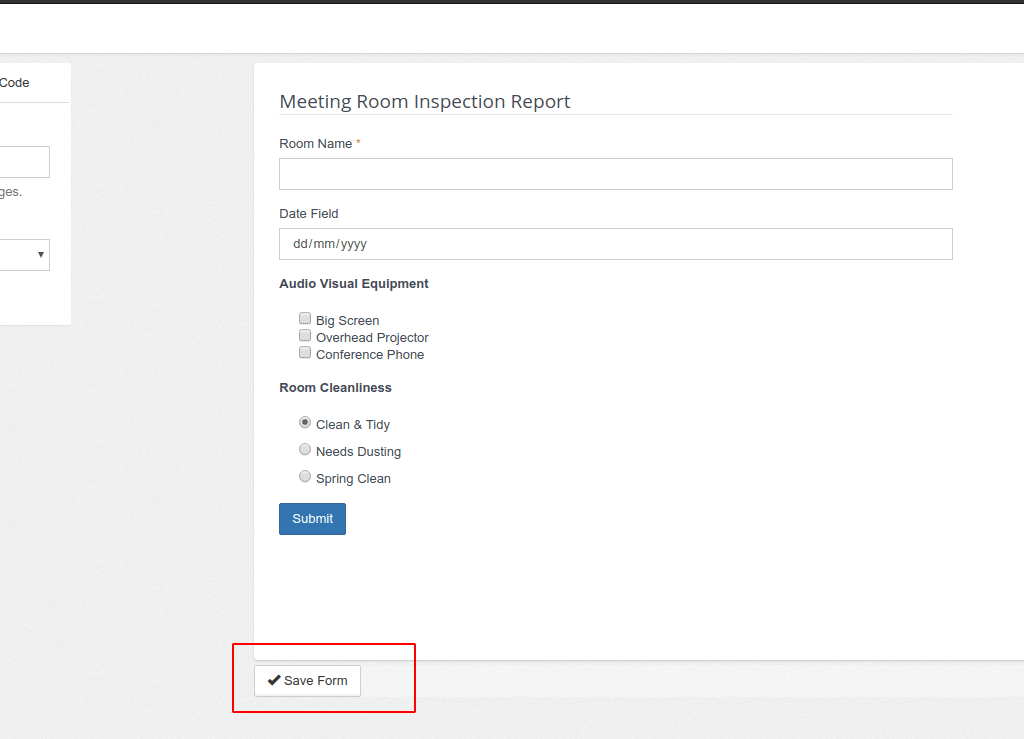
- Complete checklists on their mobile device and follow step-by-step instructions
- Check service history
- Close job orders/calls, collect signatures and start the invoice process
With a mobile app, technicians can complete a call faster, increasing the number of job order scheduled each day, giving additional revenue and that helps to grow your business.
5. Automation
What good is a field service management software without automated features??
Automation, in any industry, is an important factor in managing and growing your business.
Here are some examples of automation features and tools that your software needs in field service:
- Create and convert quotations into work orders
- Schedule/Reschedule jobs
- Accept jobs in the field
- Convert jobs into invoices
- Preventative maintenance service
- Customer updates
- Automated job reports
Business Growth with your Field Service Management Software
Field service management software is growing businesses through automation, tracking and workflow management.
Your operation can run smarter and more efficiently, all while empowering your field technicians to do their job smoothly.
If you haven’t turned to a field service management software yet, you’re missing out on chances to grow your business.
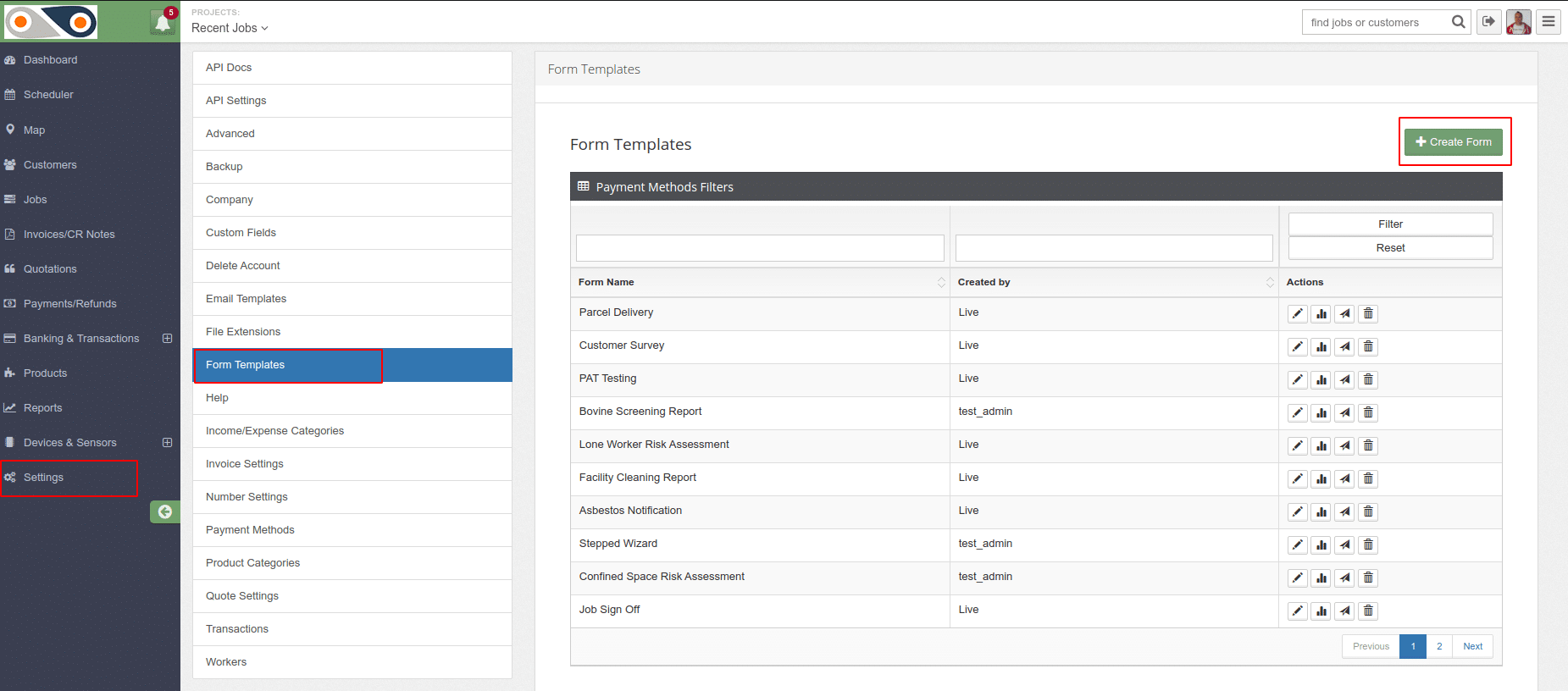
Check out FieldElite to help grow your field service business today!